Fine-grained access control in API Gateway with Cognito groups & Lambda authorizer
|
In security and access control, authentication and authorization mean two distinct but related things. Authentication verifies the identity of a user or system. Authorization determines what actions an authenticated user is allowed to perform in your system. API Gateway has built-in integration with Cognito, but it doesn’t provide any fine-grained authorization out-of-the-box. By default, a Cognito authorizer only checks if a user’s bearer token is valid and that the user belongs to the right Cognito User Pool. Here are many ways you can implement a fine-grained authorization with API Gateway. Here are three that I have come across over the years:
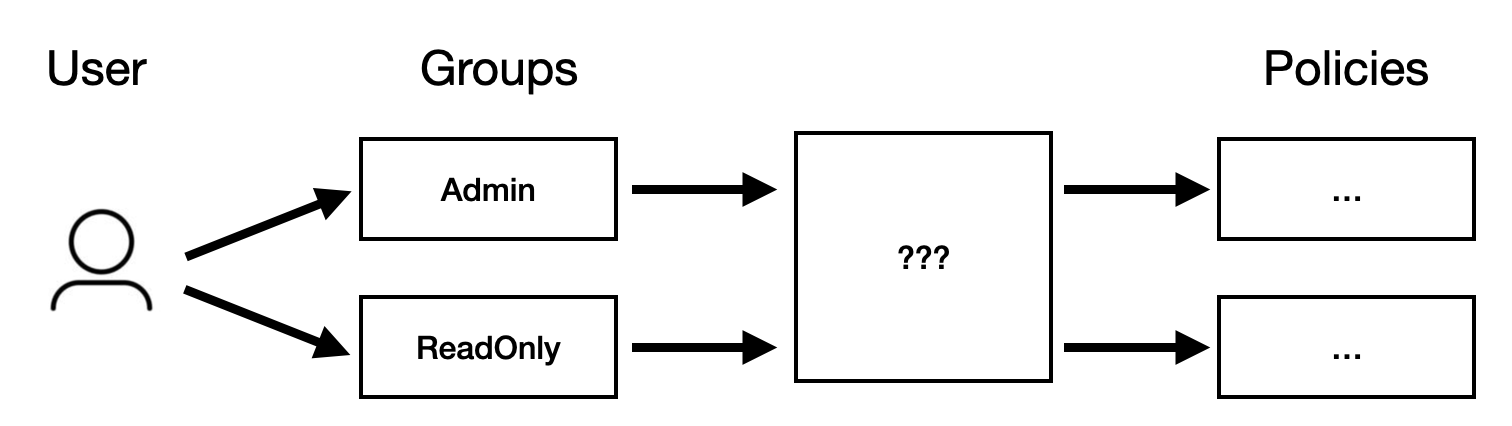
Over the next few weeks, let’s look at these approaches in-depth and then compare them at the end. Today, let’s look at Lambda authorizer with Cognito groups. Model roles with Cognito groupsIn Cognito, you can use groups to model the different roles in your system, e.g.
Users can belong to more than one group at once, just as they can have multiple roles within a system. Cognito encodes the groups a user belongs to in the ID token. If you decode the ID token, you will see something like this: Here, we can see the user belongs to both the Lambda authorizerA Lambda authorizer can use this information to generate its policy document. As a reminder, a Lambda authorizer can return a policy document like this: So, we need to take the list of groups a user belongs to and turn them into a set of policy statements.
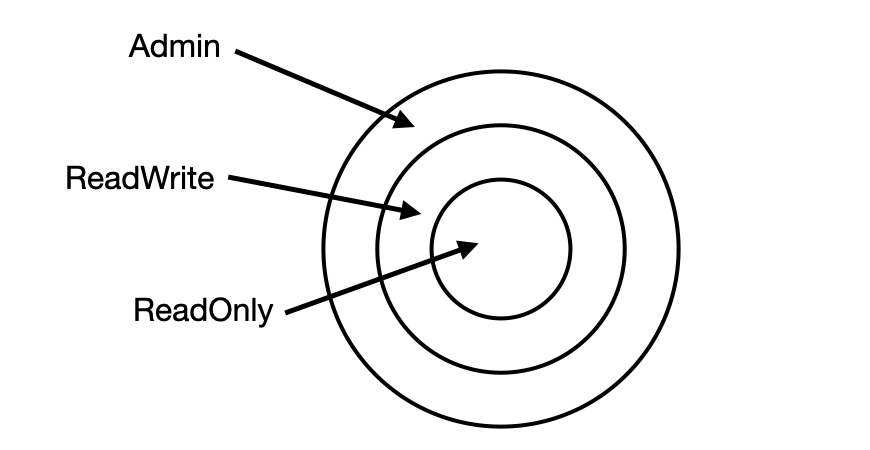
One approach is to keep a mapping in your code like this. In many systems, there are a small number of roles that supersede each other. That is, they are hierarchical, and a higher role has all the permissions of a lower role plus some.
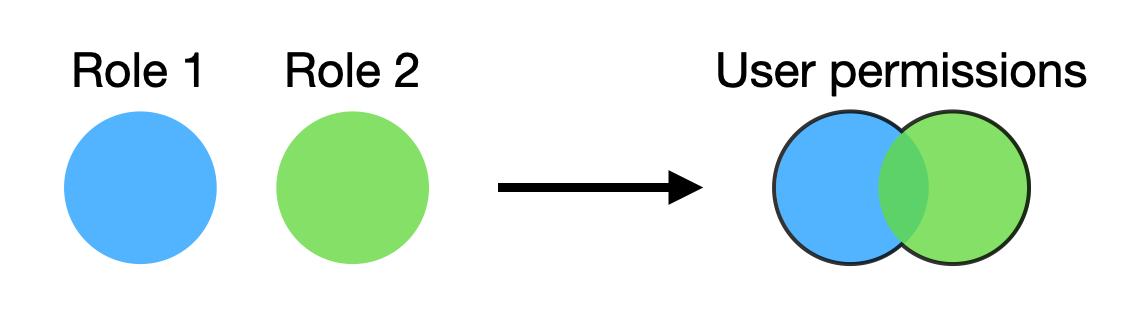
In this case, we need to find the most permissive role that the user has. But what if the roles are more lateral? That is, a user’s permissions are derived from all its roles.
Well, that’s easy enough to accommodate. ConclusionThis is my preferred approach for simple use cases. It’s easy to follow and test and makes no API calls (i.e. no extra latency overhead). Furthermore, it does not require Cognito’s Advanced Security Features, which are charged at a much higher rate [2]. This makes it a very cost-efficient approach.
However, using a Lambda authorizer means you need to think about cold starts and their impact on user experience. Also, the roles and policies are static. Whilst it’s good enough for most simple use cases, it cannot (easily) support more advanced use cases. For example, if you need to allow users to create custom roles while maintaining the tenant boundary. Amazon Verified Permissions is a better fit for more advanced use cases. More on it later. Links |
Master Serverless
Join 17K readers and level up you AWS game with just 5 mins a week.
Lambda Durable Functions is a powerful new feature, but its checkpoint + replay model has a few gotchas. Here are five to watch out for. Non-deterministic code The biggest gotcha is when the code is not deterministic. That is, it might do something different during replay. Remember, when a durable execution is replayed, the handler code is executed from the start. So the code must behave exactly the same given the same input. If you use random numbers, or timestamps to make branching...
Hi, I have just finished adding some content around Lambda Managed Instances (LMI) to my upcoming workshop. I put together a cheatsheet of the important ways that LMI is different from Lambda default and thought maybe you'd find it useful too. You can also download the PDF version below. Lambda default vs. Lambda managed instances.pdf
Two weeks ago, I gave you the biggest serverless announcements pre-re:Invent (see here). So here are the biggest serverless announcements during re:Invent 2025. Lambda Managed Instances Here’s the official announcement. A common pushback against Lambda is that “it’s expensive at scale” because: 1) Each execution environment can only process one request at a time, wasting available CPU cycles while you wait for IO response. 2) Paying for execution time is less efficient when handling thousands...