Hi, I have just finished adding some content around Lambda Managed Instances (LMI) to my upcoming workshop. I put together a cheatsheet of the important ways that LMI is different from Lambda default and thought maybe you'd find it useful too. You can also download the PDF version below. Lambda default vs. Lambda managed instances.pdf
13 days ago • 1 min read
Two weeks ago, I gave you the biggest serverless announcements pre-re:Invent (see here). So here are the biggest serverless announcements during re:Invent 2025. Lambda Managed Instances Here’s the official announcement. A common pushback against Lambda is that “it’s expensive at scale” because: 1) Each execution environment can only process one request at a time, wasting available CPU cycles while you wait for IO response. 2) Paying for execution time is less efficient when handling thousands...
about 1 month ago • 2 min read
Like London buses, we've waited years for true innovations to the Lambda platform and two came at the same time! Lambda Managed Instances Lambda Durable Functions I will be updating the Production-Ready Serverless workshop to cover these new features in the January cohort. For now, let's take a closer look at Lambda Managed Instances, why you should care and when to use it. Introducing Lambda Managed Instances A common pushback against Lambda is that "it's expensive at scale" because: 1) Each...
about 2 months ago • 2 min read
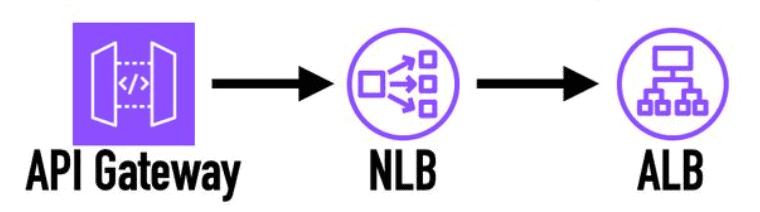
re:Invent is almost upon us. A number of significant features have already been announced ahead of the main event. Here is a list of the serverless-related announcements so far that you should know about. API Gateway integration with ALB (without NLB) Here’s the official announcement. This is one of those things that everyone assumed just works, but never did. Until now, if you want to connect API Gateway to an ALB, you have to first go through an NLB. With the introduction of VPC Link v2,...
about 2 months ago • 6 min read
The DNS failure was the first symptom, not the root cause of the recent AWS outage. The root cause was a race condition in an internal DynamoDB microservice that automates DNS record management for the regional cells of DynamoDB. Like many AWS services, DynamoDB has a cell-based architecture. (see my conversation with Khawaja Shams, who used to lead the DynamoDB team, on this topic) Every cell has an automated system that keeps its DNS entries in sync. That automation system has two main...
3 months ago • 1 min read
AppSync doesn’t allow unauthenticated API calls. To allow users to call your API without first authenticating themselves, you must mimic the behaviour using one of the available authorization methods [1]. In this post, let’s look at three ways to implement unauthenticated GraphQL operations with AppSync and their pros & cons. API Keys To use API keys, you need to: Add an API Key in AppSync. Pass the API Key in the x-api-key header. That’s it! It’s the easiest and most common way to implement...
7 months ago • 2 min read
A common challenge when building APIs is supporting multiple live versions without letting the system turn into an unmaintainable mess. You need to keep older versions running for existing clients, roll out new versions safely, and avoid breaking changes that might take down production. And you need to do all that without duplicating too much infrastructure or introducing spaghetti logic inside your code. There’s no official pattern for versioning APIs in API Gateway + Lambda. API Gateway...
8 months ago • 3 min read
I recently shared six event versioning strategies for event-driven architectures [1]. In response to this, Marty Pitt reached out and showed me how Orbital [2] and Taxi [3] use semantic tags to eliminate schema coupling in event-driven architectures and simplify the schema management. It's a novel way to manage schema evolution, and I want to share what I learnt with you. Problems with Schema Coupling In an event-driven architecture, event consumers are typically coupled to the schema of the...
9 months ago • 2 min read
Last week, we looked at 6 ways to version event schemas [1] and found the best solution is to avoid breaking changes and minimise the need for versioning. But how exactly do you do that? How can you prevent accidental breaking changes from creeping in? You can detect and stop breaking changes: At runtime, when the events are ingested; During development, when schema changes are made; Or a combination of both! Here are three approaches you should consider. 1. Consumer-Driven Contracts In...
9 months ago • 3 min read